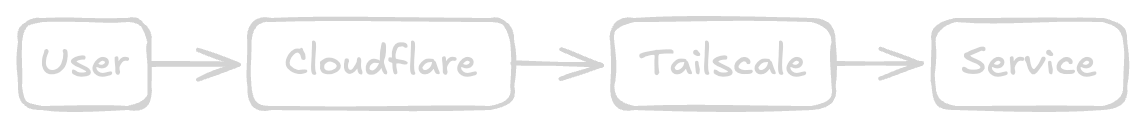
Part 2: Trash Guide Goodness in my Unraid Server
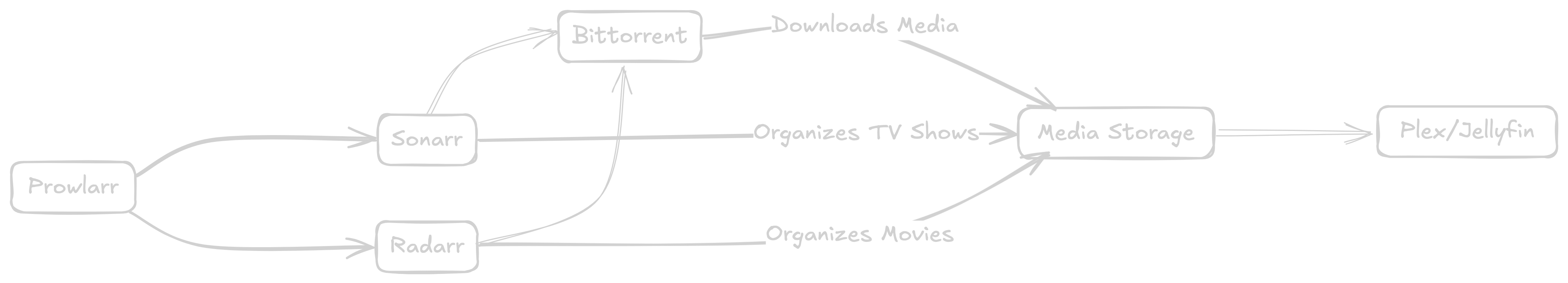
TL;DR: Don’t do anything illegal. Jump to the Totally Legal Use Cases section for all the cool legal use-cases. Intro In Part 1, I walked through building my Unraid server — migrating from a mini-PC and laying the hardware foundation for a reliable homelab. The goal: build a flexible, automated media server that runs cleanly and requires minimal manual intervention. In this post, I’ll cover how I automated everything using Docker, Trash Guides, and a suite of containers — including Plex, Jellyfin, Sonarr, Radarr, and more — all working together to provide a seamless media experience. ...